Netdiscover windows equivalent, List Windows shares, again you can also specify username -u and password -p. Enum4linux -s shares.txt target-ip. Perform a dictionary attack, if the server doesn't let you retrieve a share list. Enum4linux -o target-ip. Pulls OS information using smbclient, this can pull the service pack version on some versions of Windows. Enum4linux -i target-ip. Evidenced through the classic 'I'm a Mac' ads. A network discovery tool that sends ARP packets to a target device or IP range and sniffs the network for responses to identify the.
日期:2019-06-27 15:54:19 作者:Bay0net 介绍:在 mac os 下,如何安装 netdiscover 及基本使用方法 0x01、当前环境 MAC os 10.14.4 已安.
Overview
Objective : Get Flag
OVA link: https://www.vulnhub.com/entry/mr-robot-1,151/
Tools used: netdiscover, nmap, nikto, metasploit, truecrack, veracrypt
To start, I just ran a quick netdiscover to get the DroopyOS IP. The highlighted IP is the one we're after.
Running a quick version scan shows up an open port of 80, which would imply a web server of some sort. Let's see what that web page looks like!
Upon loading the webpage, we can see a generic drupal login page (the logo above home is the drupal logo). Drupal is notorious for vulnerabilities so we should have some smooth sailing (hopefully?)
I clicked around the 'create new account' and 'request new password' links but nothing obvious stands out as a hint or direction. To help find some vulnerabilities, I ran a nikto scan with the corresponding output listed below.
We have a lot of information to parse through. The most immediately obvious clue is 'robots.txt', which is referenced multiple times. Loading up this page should some interesting information, as seen below. We can see some file structure we can go through as well as some specific files to checkout.
The 'giveaway' here is the /CHANGELOG.txt. This file is commonly used to show the current Drupal version with corresponding patch notes. We can see here that Drupal 7.30 is running.
A little googling about this version of Drupal, shows a vulnerability via CVE-2014-3704, which has a nicely prepackaged Metasploit exploit dubbed 'Drupageddon'. We can go boot up the msfconsole and see what the options are. Looks like we only need to add the RHOST (192.168.1.137).
This may have been the easiest shell I've ever obtained. I almost feel guily.. perhaps later I'll see if I can code the exploit by hand and see if I can get it to work. Anyways... we got a shell:
Interestingly enough, we have a /tmp folder we can use to get some executable exploits running.
Now we just have to figure out what we have to work with. For this situation, I'm going to call the normal bash shell instead of using meterpreter. The listed below are the commands I ran to just gather some information and find an exploit. It looks like searchsploit found what we need: Linux Kernel 3.13.0 < 3.19 (Ubuntu 12.04/14.04/14.10/15.04) - 'overlayfs' Local Root Shell.
I usually make seperate directories per Vulnhub VM. To get the exploit onto the DroopyOS box, I'm going to copy the exploit to my working directory then download it to the /tmp folder on the target host via meterpreter. I like copying the exploits per use case. This way if I have to edit the exploit and break it, I can always fallback to the original.
To emphasize, you can notice the permission changes below. The 'x' addition means essentially any user can execute the file.
We now have a raw .c file to compile. You can type 'gcc --version' to check if gcc is installed on the system. A quick compile and execute later, we have root! We're done now! RIGHT?!
I went into the /root/ folder aaand we have an .tc file. This is a file extension for a TrueCrypt container, which I guess we have to brute force?
The only hint we really have to go on is on the Vulnhub page where the author gives the following two hints:
I'm going to assume the rockyou wordlist is needed for the truecrypt file. The email hint is also worth looking into. (fast forward awhile) I found the 'email hint' in '/var/mail/':
Ok so now we obviously have to you use rockyou dictionary and we need to get that .tc file on our Kali host. To do this, I copied (as root) the dave.tc file to the /tmp directory. I then downloaded it via meterpreter as follows:
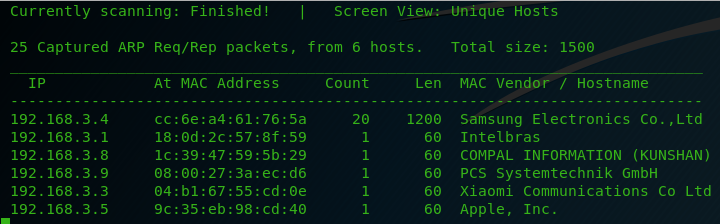
Netdiscover Mac Os Versions
Now we need to prepare the rockyou wordlist. If you're on a new version of Kali, you need to extract it for use. The default location is '/usr/share/wordlists/rockyou.txt.gz'. I like keeping all my wordlists in '/root/Wordlists/'. We can see that this file is huge.. namely 14344392 lines long. From the email we know we can remove all passwords longer than 11 characters. I shortened the list using awk:
I then grepped that list for all entries with the string 'academy' in the password. The last step would (hopefully) be cracking the trucrypt file. Kali has a preinstalled tool called 'Truecrack' for just this purpose. Syntax as follows:
This did not produce any results, however, I tried the 'sha512' hash via :
We got the truecrypt password! Since truecrypt is no longer supported, I downloaded Veracrypt and plugged in the password. We can use this password, enable Truecrypt mode, the hash type, and open the Truecrypt container!
Going into the file structure, there's a couple directories and images but if you do a 'ls -a' you can see hidden directories. Going into '/media/veracrypt1/.secret/.top' will reveal the following flag:
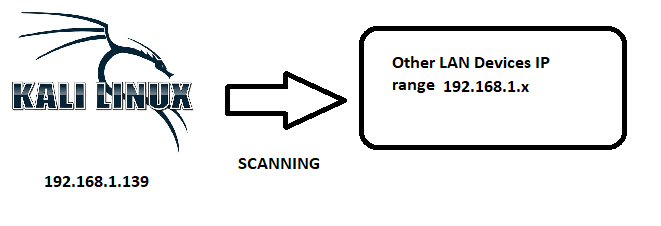
Quite often, people will ask me where they should start in Hacking. Oh my gosh! There are soooo many topics, subjects, ideas, things to memorize, things to mess with, etc… It is much too difficult to tell someone where to start. Ummmm… I guess I might say you can start with reconnaissance. Or, if stuff in this article doesn’t seem to make sense, you should probably start with a networking basics course. So, first you will want to find out about the other computers around you on a network. There are numerous ways to do this, but in this tutorial I will show you how to use a tool built into BackTrack / Kali that leverages Address Resolution Protocol or ARP to discover live hosts on the network.
As you know, ARP is used to map MAC addresses to IP addresses on an internal network. The router and switches send out broadcast ARP requests to all the MAC addresses on the network asking them to respond with their IP addresses. Each system will then respond with their IP address and the switch or other device will then create a small database that maps the MAC to the IP address, so that it it knows “who is who”.
We can use this same protocol to discover the IP addresses on a corporate, educational, wireless or other network by using Netdiscover. Its a simple tool that simply sends out ARP’s—just like a switch or router would—asking for everyone’s IP address on the network. In this way, we can gather the IP’s we need and then to attack those machines with a MitM attack, Metasploit or other attack.
Before we get started, let’s open Wireshark and look at some normal network traffic. As you can see in the screenshot below, once we open Wireshark and just wait a short while, I begin to send ARP requests. Packets 2113 and 2114 show an ARP exchange. If you look at 2113 and then scan across to the info section to the far right, you can see “who has 192.168.1.1?”. In the following packet, we see the response “192.168.1.1 is at xx:xx:xx:xx:xx:xx”. That is normal ARP traffic.
We can now create a filter in Wireshark to just look for ARP tarffic by typing “arp” in the filter window at the upper left. Now, all we see is ARP traffic as Wireshark has filtered out everything else.
Now that we see a bit of normal ARP traffic and how it works, let’s fire up BackTrack and abuse the ARP protocol to learn the IP and MAC addresses of everyone on the network.
Step 1: Find Netdiscover
We can find netdiscover by going to either Backtrack or Kali.
In Kali, go to the Kali Linux Menu –> Information Gathering –> Live Host Identification –>Netdiscover

In Backtrack, go to the Backtrack Menu –> Information Gathering –> Network Analysis –> Identify Live Hosts –> Netdiscover.
Step 2: Open Netdiscover
When we click on netdiscover, it opens a screen like that below and displays some basic help. Netdiscover is a relatively simple tool, so there are not a lot of options.
Step 3: Netdiscover Command
To discover the IP’s on an internal network, we will usually want to scan a range of IP addresses. In netdiscover, we can use the -r switch (for range) and then in CIDR notation provide it the network range we want it to scan. In the command below, we are asking netdiscover to find all the live hosts with IP addresses between 192.168.1.1 to 192.168.1.255. We do this by typing;
netdiscover -r 192.168.1.0/24
Netdiscover Mac Os X
Step 4: Activate Netdiscover
Mac Os Download
As soon as we enter the command, netdiscover begins sending out ARP requests over the network and then logging the results on our screen. The process is live and interactive, so that as soon as new machines come on the network they pop up on our screen.
Netdiscover Mac Os High Sierra
Netdiscover is a simple but powerful tool that uses the ARP protocol to discover live network hosts. As long as you are connected to the network and ARP is enabled on the network, you should be able to discover every live host’s IP and MAC address. Once you have those, then you can begin your strategy of exploiting those hosts.